The electronics test engineer was the first to enter the lab that morning. He turned on the radio and thought to himself “That’s the third time I’ve heard that song today, and it’s so monotonous.” It was time for a new station. He turned the tuning knob and soon realized he was scanning the AM band. “Why do the lab techs always insist on listening to AM stations?” He switched the radio to the FM band and was soon listening to his favorite golden oldies station. OK, it was time to get to work.
He applied power to the unit under test and a horrible buzzing sound filled the room. It was coming from the radio. He tried other FM stations on the radio. Each one was accompanied by the buzzing sound. “Oh…now I understand,” he thought. The prototype has been generating electromagnetic interference. That interference has been garbling the music on the FM stations. The lab techs were probably adapting to this by only listening to the AM stations.
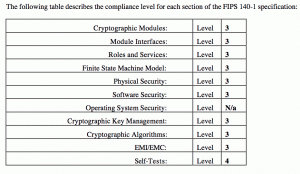
To test his theory, he switched the radio back to the AM band, trying various stations. Each AM station came through loud and clear. The electronics test engineer had a problem, because his company would not be able to sell a device that interfered with FM broadcasts. He knew the prototype would eventually be sent to a special testing lab for an FCC certification. The electromagnetic compatibility (EMC) test technicians there would also detect the interference. He hoped he would be able to find the source of the problem and fix it before schedules and budgets were negatively impacted.
To be continued in “Egad… Electronic Interference is Emanating From the Prototype! (Part 2)”